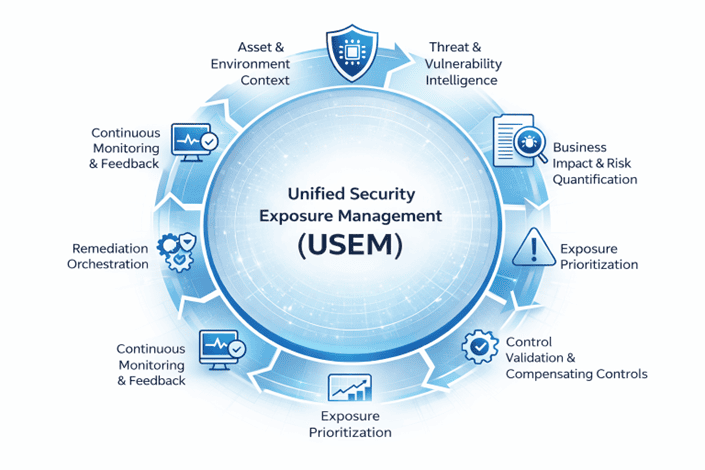
What USEM Is
CAASM is the authoritative intelligence layer for cybersecurity and risk programs. It continuously identifies, normalizes, and correlates all enterprise assets - IT, OT, IoT, cloud, and AI - into a single, trusted source of truth.
CAASM answers one foundational question:
“What exists in our environment, who owns it, and how is it exposed?”
Without CAASM, every downstream security, risk, and compliance decision is built on assumptions.
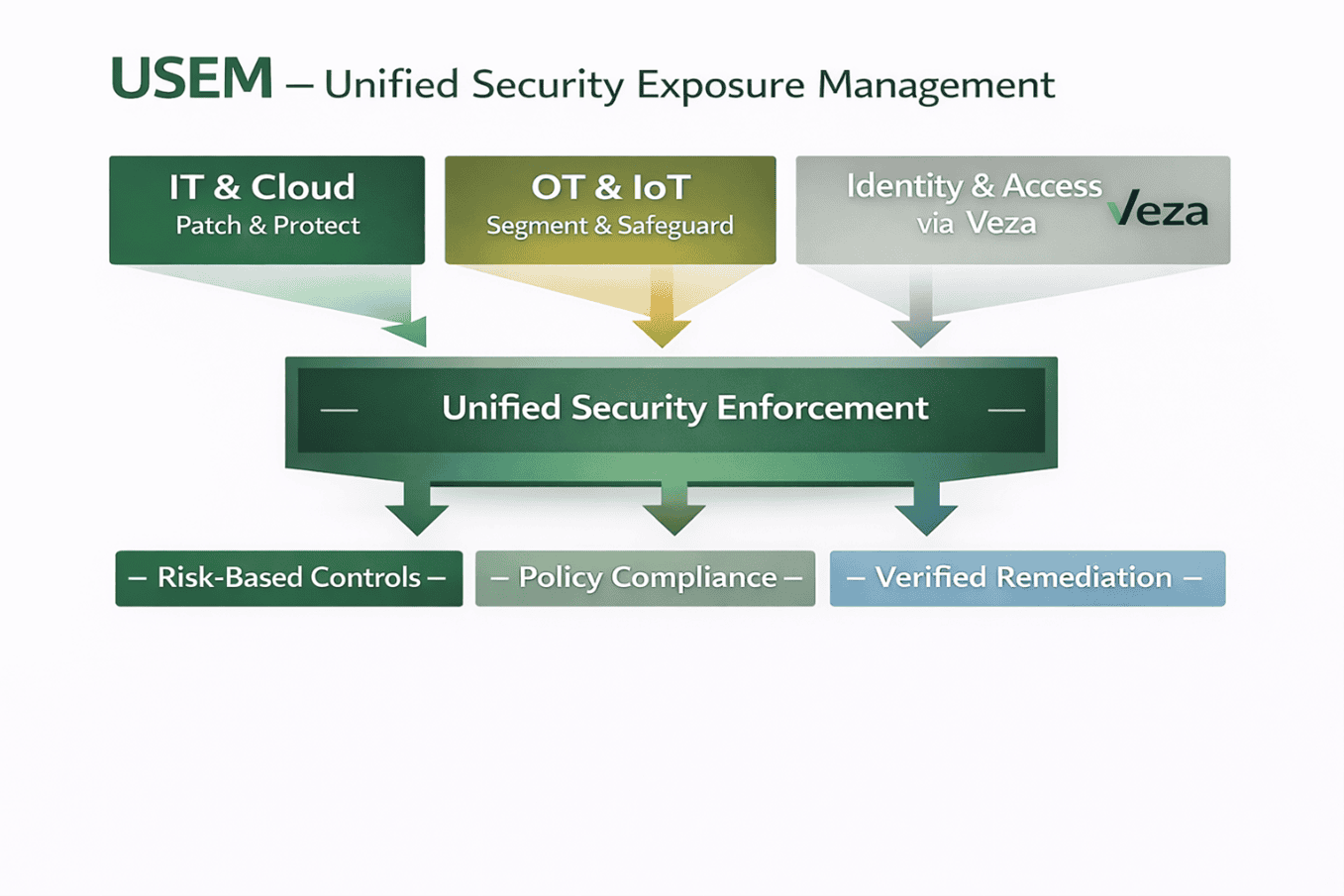
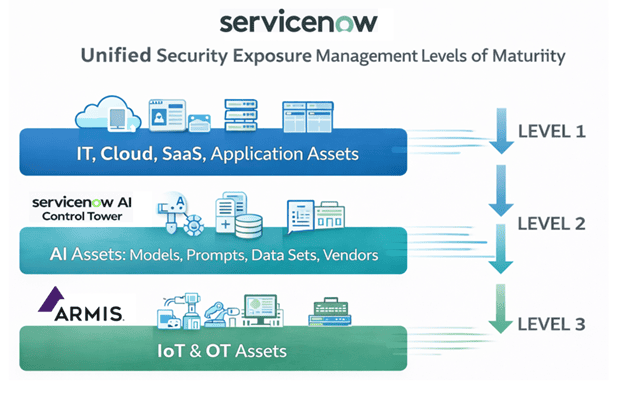
Where USEM Operates
- IT and cloud security controls
- OT and IoT compensating controls
- OT and IoT compensating controls
- AI system access and policy enforcement
How USEM Works (Program Mechanics)

Policy-Aware Enforcement
Controls respect:
- Operational constraints
- Safety requirements
- Regulatory obligations

Identity Enforcement
Using Veza, USEM reduces:
- Excess privilege
- Toxic access paths
- AI system overexposure

OT & AI-Safe Mitigation
USEM emphasizes:
- Segmentation
- Monitoring
- Compensating controls where patching is unsafe

Control Mapping
Exposure types are mapped to appropriate controls.

Verification & Evidence

Why USEM Is Required
- Vulnerability programs prioritize the wrong assets
- Tickets close without reducing risk
- OT systems cannot be patched
- AI systems lack access governance
- Identity risk remains unchecked
USEM bridges intent and impact.
Ethics & Responsible Use
- Reduce ticket volume and resolution times
Safety-first enforcement (especially OT)
Least-privilege access without productivity harm
AI access controls that preserve innovation
Transparency and auditability of actions
USEM ensures security does not become harm.

Framework & Regulatory Alignment
USEM supports:
- NIST CSF 2.0 - Protect and Respond functions
- NIST SP 800-53 - AC, CM, CP, IR controls
- IEC 62443 - OT-safe enforcement
- NIST AI RMF - Govern and Manage functions
- Zero Trust Architecture - Continuous verification
- EU AI Act - Access and use controls
ROI & Business Value
USEM delivers ROI by:
- Eliminating redundant tooling and manual inventories
- Ensuring remediation effort actually reduces exposure
- Preventing outages caused by unsafe fixes
- Reducing breach blast radius
- Strengthening audit defensibility
- Enabling automation without loss of control
USEM turns security activity into measurable risk reduction.

Talk to an expert
Interested To Know How
We Can Help







