What CAASM Is
CAASM is the authoritative intelligence layer for cybersecurity and risk programs. It continuously identifies, normalizes, and correlates all enterprise assets - IT, OT, IoT, cloud, and AI - into a single, trusted source of truth.
CAASM answers one foundational question:
“What exists in our environment, who owns it, and how is it exposed?”
Without CAASM, every downstream security, risk, and compliance decision is built on assumptions.
“This isn’t about more data - it’s about defensible truth.”
“Inventories answer ‘what exists.’
Truth engines answer ‘what’s real, what changed, and who’s accountable.’”
“This isn’t another inventory - it’s a truth engine.
ServiceNow doesn’t replace your tools; it records what they collectively reveal about assets, access, and exposure over time.
That’s why it works in regulated, board-sensitive environments - because accountability stays human, execution stays distributed, and truth stays consistent.”
“Everything feeds in, governance happens once, and action fans back out through IRM, SecOps, OT, and AI workflows.”
This is not services sprawl.
This is risk gravity pulling work into the platform.
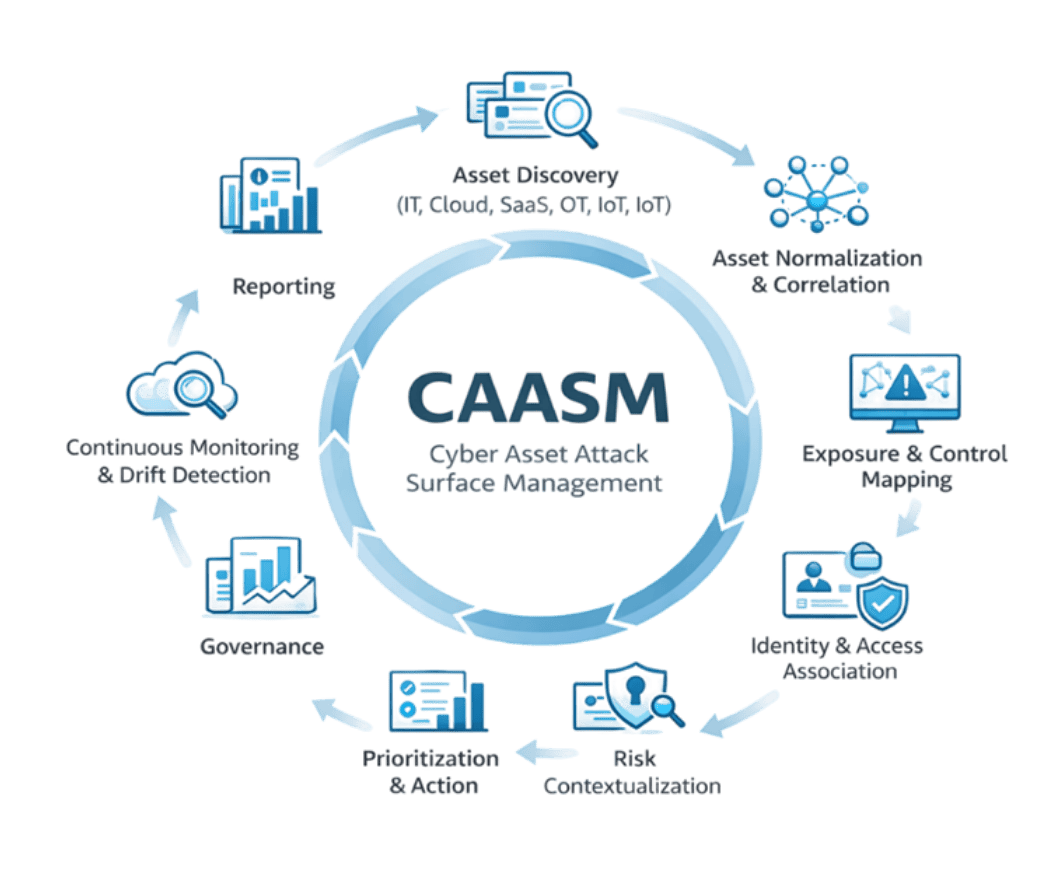
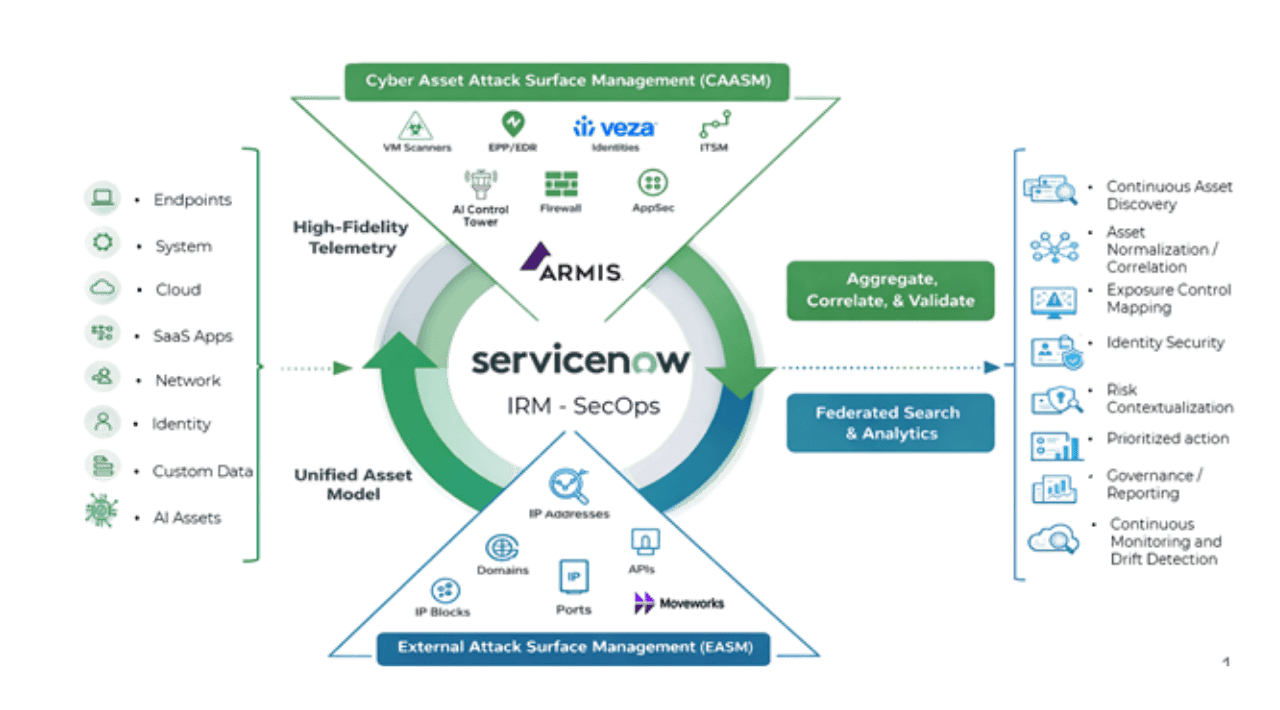
Where CAASM Operates
- Asset discovery systems
- Identity and access systems
- AI inventory and governance systems
- The enterprise CMDB (system of record)
Primary feeds include:
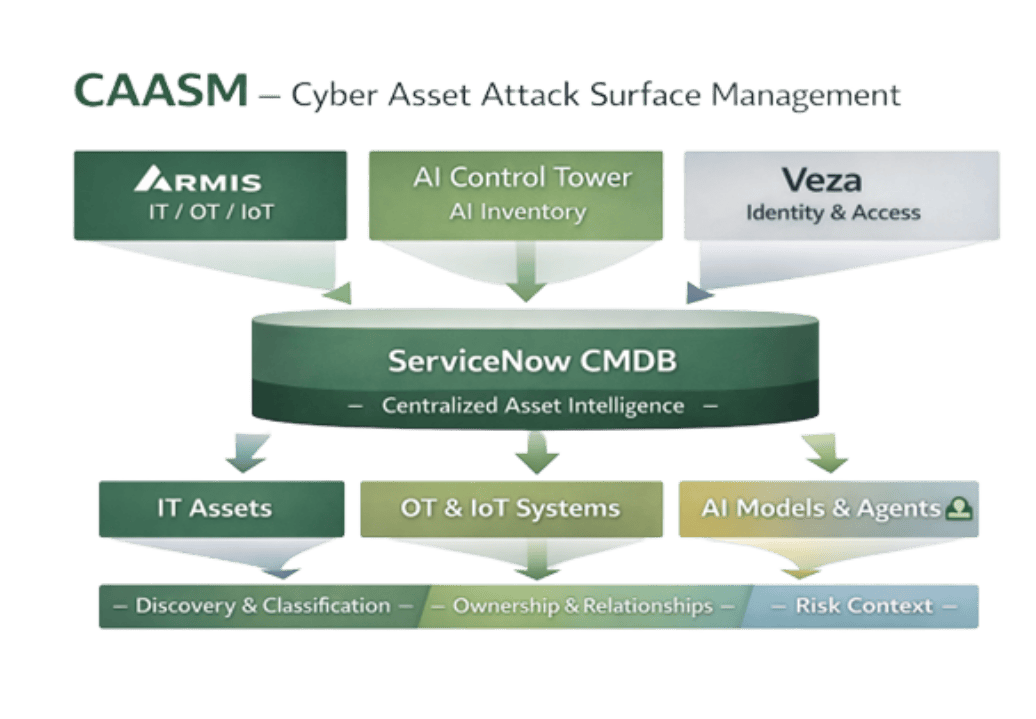
- Armis for IT, OT, IoT, and unmanaged asset discovery
- ServiceNow AI Control Tower for AI models, agents, pipelines, and use cases
- Veza for authorization and access relationships
Where CAASM Operates

Discovery
Assets are discovered continuously, not periodically.

Normalization

Exposure Readiness
The output is an exposure-ready asset graph consumable by CTEM and USEM.

Relationship Mapping
Assets are linked to:
- Owners
- Applications
- Data
- Identities and access paths

Classification
Assets are categorized by:
- Type (IT, OT, IoT, AI)
- Business function
- Criticality
- Regulatory impact

Why CAASM Is Required
- Vulnerability programs prioritize the wrong assets
- Identity reviews lack context
- AI governance misses shadow AI
- Audits rely on sampling and guesswork
- Boards receive misleading risk metrics
CAASM eliminates unknown assets, false confidence, and manual reconciliation.
Ethics & Responsible Use
- Reduce ticket volume and resolution times
- Asset visibility must not become employee surveillance
- Discovery must respect privacy and legal boundaries
- AI assets must be classified with explain ability and accountability.
CAASM supports responsible security by ensuring decisions are made on facts, not fear.

Framework & Regulatory Alignment
CAASM directly supports:
- NIST CSF 2.0 - Asset Management, Risk Context
- NIST AI RMF - AI system inventory and governance
- ISO 27001 / 27002 - Asset ownership and classification
- IEC 62443 - OT asset identification
- SOX / HIPAA / PCI DSS - Scope accuracy
- EU AI Act - AI system inventory and risk classification
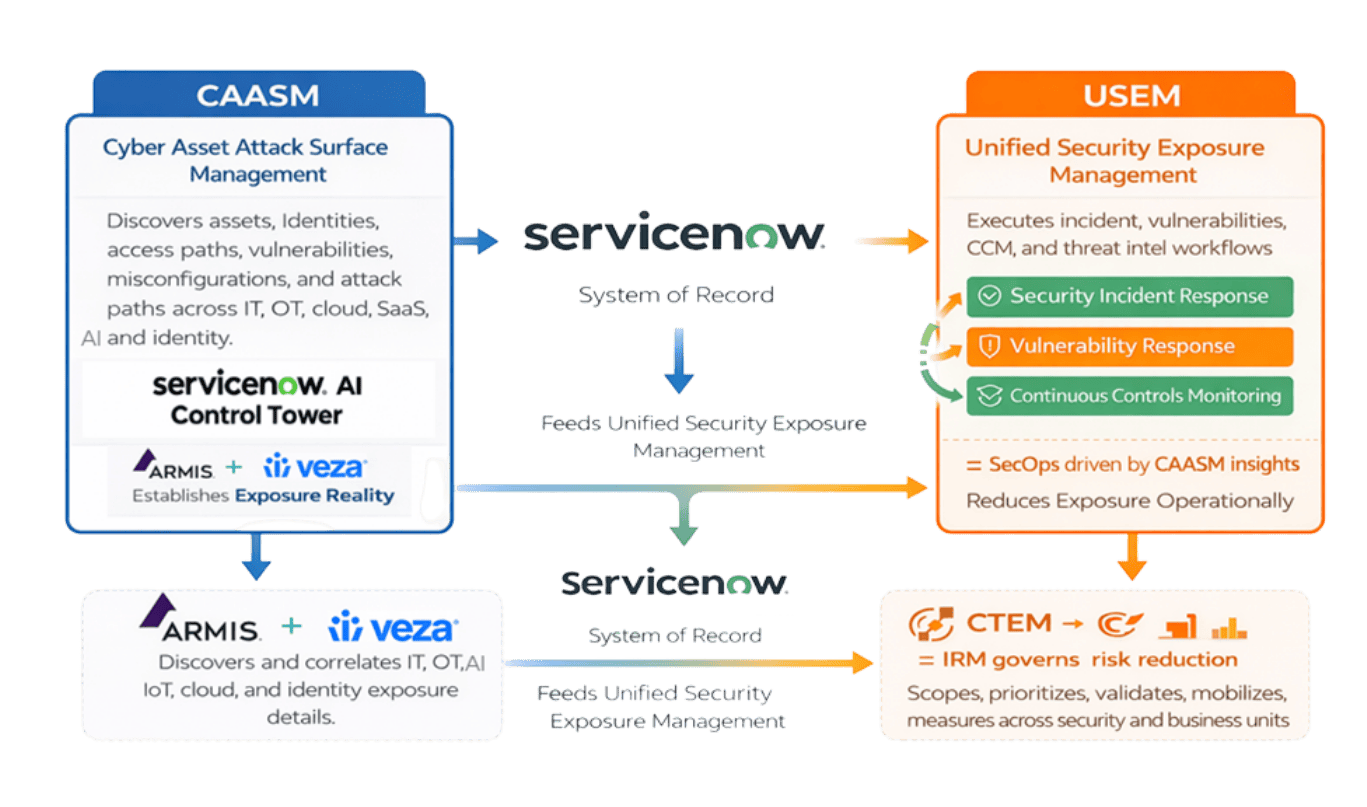
ROI & Business Value
CAASM delivers ROI by:
- Eliminating redundant tooling and manual inventories
- Reducing time spent reconciling asset data
- Improving vulnerability prioritization accuracy
- Preventing audit findings caused by incomplete scope
- Enabling automation downstream
CAASM is the highest-leverage investment in cybersecurity - it multiplies the value of every control that follows.
Talk to an expert
Interested To Know How
We Can Help







