What CTEM Is
CTEM is a continuous decision-making discipline that identifies, prioritizes, and tracks security exposures based on real-world risk, not theoretical severity.
“Given what we have and how it’s exposed, what matters most right now?”


Where CTEM Operates
ServiceNow SecOps (vulnerability, incident, response)
ServiceNow IRM (risk scenarios, KRIs, reporting)
How CTEM Works (Program Mechanics)

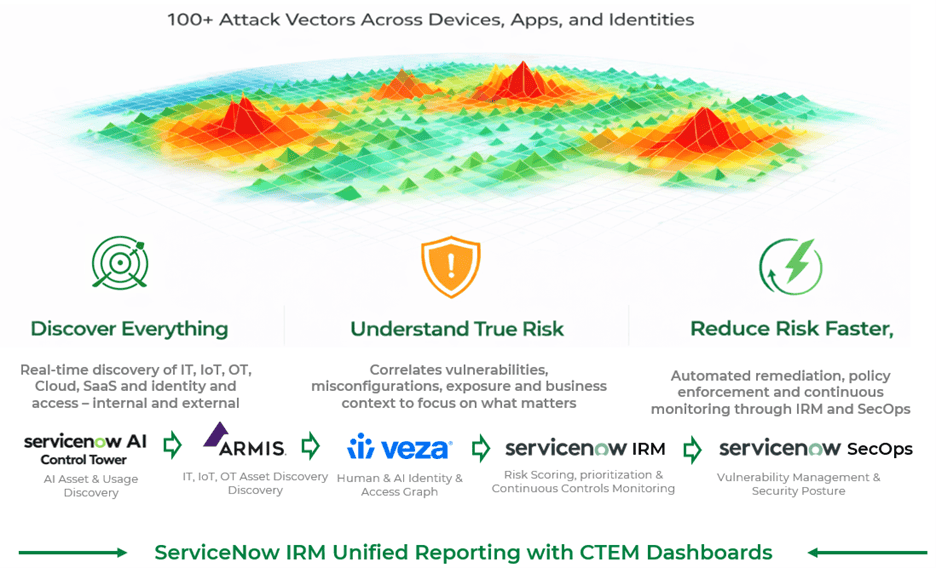
Exposure Aggregation
Vulnerabilities, misconfigurations, identity risk, and AI risk are aggregated.

Risk-Based Prioritization

Action Orchestration
CTEM drives remediation workflows into IT, OT, cloud, and identity teams.

Contextual Correlation
Exposure is correlated with:
- Asset criticality (from CAASM)
- Identity access paths (from Veza)
- AI risk classification (from AI Control Tower)
- Threat intelligence and exploitability

Outcome Measurement

Why CTEM Is Required
It treats all assets equally
It cannot explain risk to executives
It overwhelms teams with noise
It ignores identity and AI risk
CTEM aligns security effort with business reality.
Ethics & Responsible Use
Avoiding “security theater”
Preventing burnout through intelligent prioritization
Preventing bias in risk scoring
Ensuring AI-driven prioritization is explainable and auditable
CTEM supports ethical security operations by focusing on meaningful risk reduction, not metrics inflation.

Framework & Regulatory Alignment
CTEM aligns with:
- NIST CSF 2.0 - Continuous risk management
- NIST SP 800-53 - RA, SI, IR controls
- NIST AI RMF - Risk measurement and monitoring
- ISO 27001 - Risk treatment lifecycle
- SEC Cyber Disclosure Rules - Material risk tracking
- Cyber Insurance Underwriting - Exposure-based reporting

ROI & Business Value
CTEM delivers ROI by:
Reducing MTTR
Cutting vulnerability backlogs by focusing on what matters
Improving executive trust in security metrics
Reducing breach likelihood
CAASM is the highest-leverage investment in cybersecurity - it multiplies the value of every control that follows.
Talk to an expert
Interested To Know How
We Can Help







