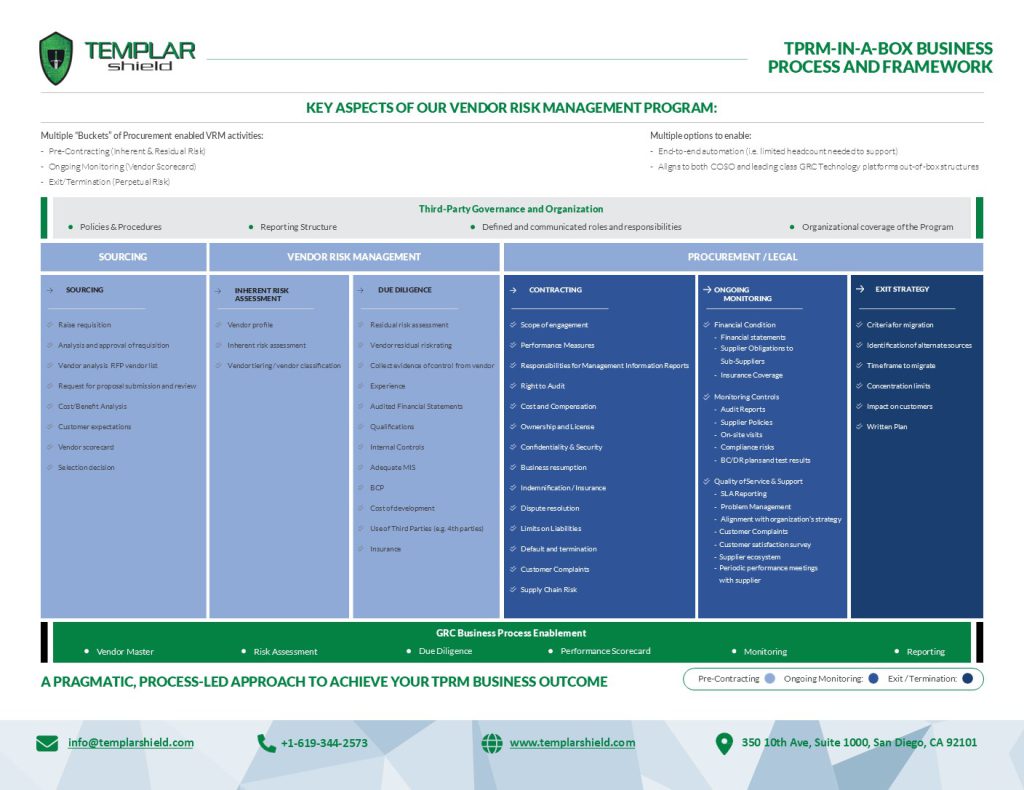
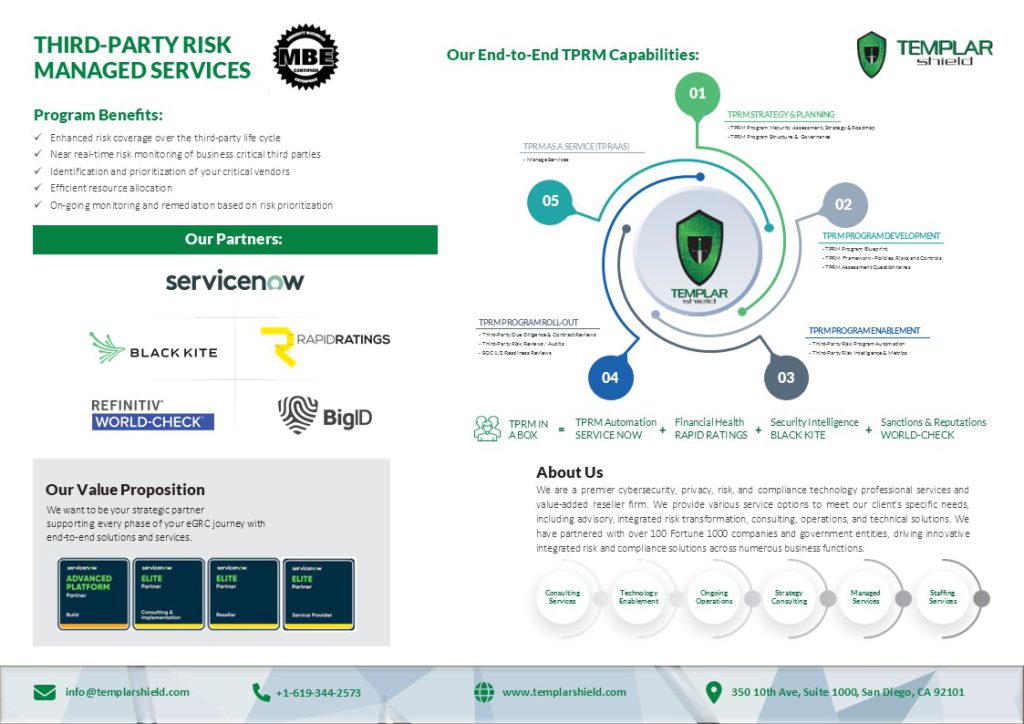
TPRM-IN-A-BOX BUSINESS PROCESS AND FRAMEWORK

Navigating the complexities of federal regulations, compliance frameworks, and evolving technological challenges is a monumental task for US State agencies. Templar Shield, in partnership with ServiceNow, brings a transformative managed service program tailored specifically to streamline, enhance, and secure these very operations for US State and their subsidiary agencies.




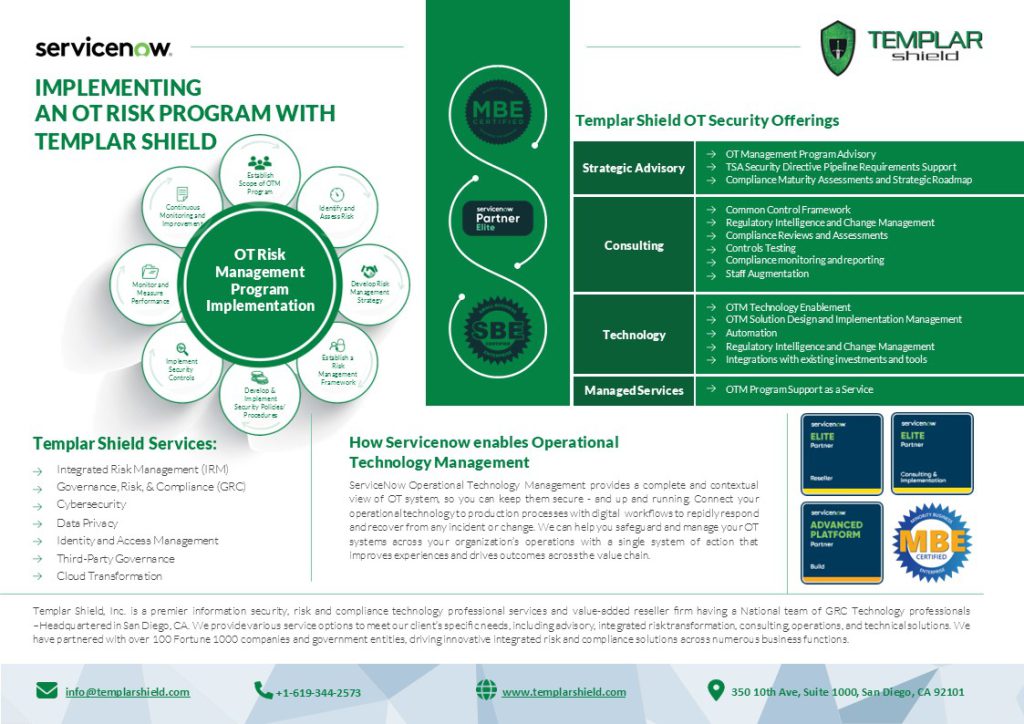
Templar Shield is an elite cybersecurity, privacy, risk, and compliance technology professional services and value-added reseller firm.
We provide various service options to meet our client’s specific needs, including advisory, integrated risk transformation, consulting, operations, and technical solutions. We have partnered with over 100 Fortune 1000 companies and government entities, driving innovative integrated risk and compliance solutions across numerous business functions.


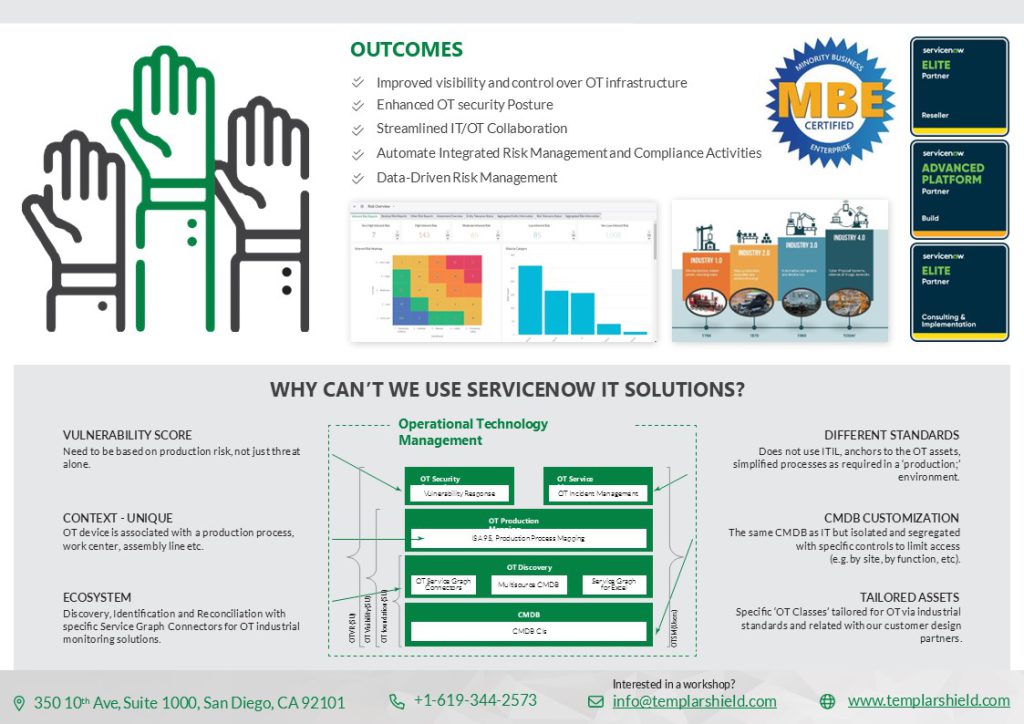
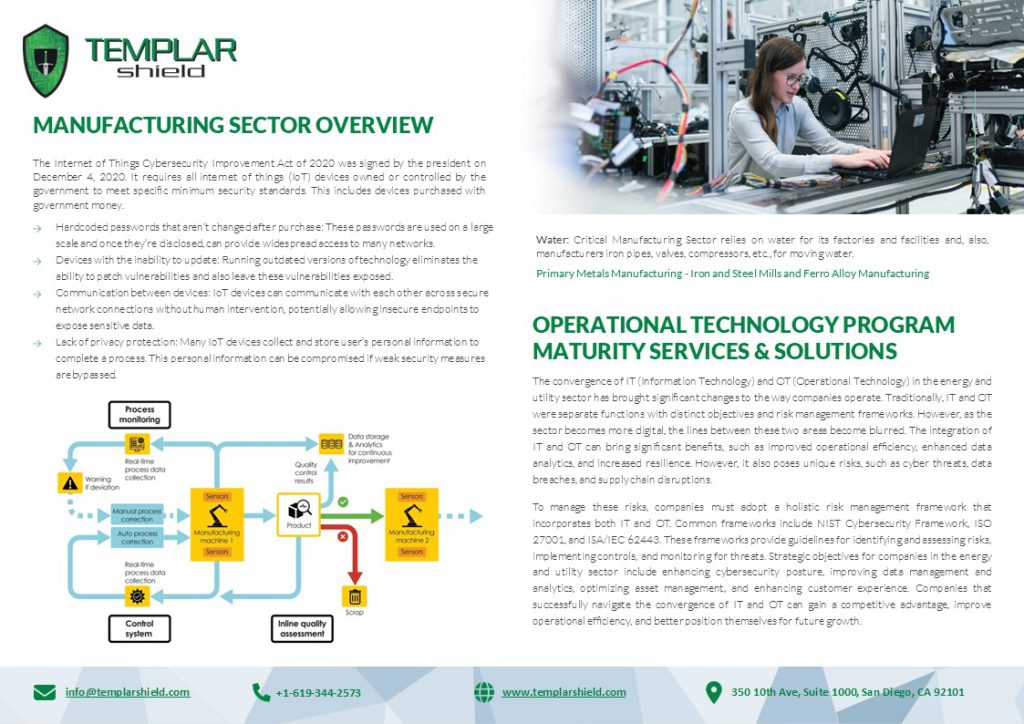
The convergence of IT (Information Technology) and OT (Operational Technology) in the energy and utility sector has brought significant changes to the way companies operate. Traditionally, IT and OT were separate functions with distinct objectives and risk management frameworks. However, as the sector becomes more digital, the lines between these two areas become blurred.

Managing third-party risks is challenging due to the excessive time and resources required to
identify and mitigate those risks. Necessary activities such as vendor liaison and follow–up
processes consume even more resource bandwidth during the course of those particular risk
assessments.

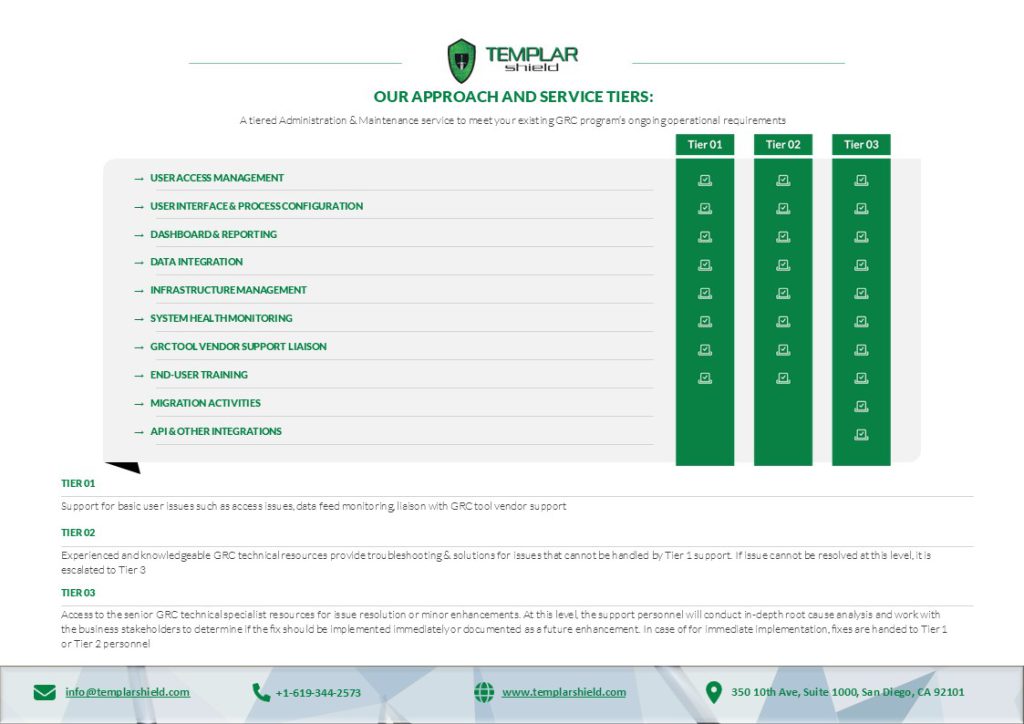
An effective GRC technology enablement program is a well-balanced combination of people, process, and technology. Once deployed, a successful platform requires the right maintenance support continue to meet end user performance expectations and deliver efficiencies.

In the Banking and Financial Services Industry, having a robust ERM program is essential due to the inherent risks associated with financial transactions. These risks can include market risk, credit risk, operational risk, and regulatory risk, among others.


By attending this workshop, professionals responsible for protecting our nations critical infrastructure will gain valuable insights into how ServiceNow can empower IT/OT convergence.